The computer systems of online business are always prone to new security threats. Websites that handle important information like credit card data are the preferred targets of cyber criminals and disgruntled employees. Protecting important information of the customers is critical to earning trust and maintaining revenue. The cost of security breach is quite high, not only in the dollars, but also in the form of company reputation. In addition to this, companies may need to comply with the standards that are established by the payment card company for which they process all their transactions. Stringent computer security testing solutions can help the companies to build, deliver and maintain their databases and applications resist hacking.
Application developers should be well-aware of the different types of attacks and threats to build more secure applications, and whenever possible, they should add defenses to their systems. Security testing during the development stage can also help to identify the possible areas of exposure so that they can be addressed early on. Further, it is less expensive to build application security from starting, rather than needing to rework an app when it is almost completed.
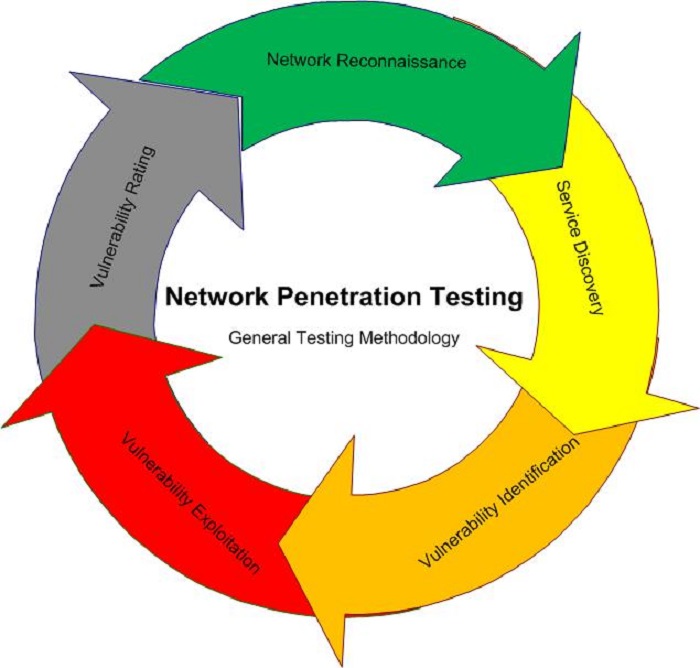
One of the standard and the most reliable tools used in security testing is called penetration testing. Penetration testing emulates the computer system attack methods that a hacker might use. The penetration testing tools automate some of these processes, which results in more effective and faster tests. This testing should be conducted with care when targeting production systems. An effective penetration testing can also be done on the development environment. There are various penetration testing services in India that can help you to conduct this testing in prompt and reliable manner.
Even when penetration testing tools are used, there could still be value in conducting a review of source code of software. In the review process, system security issues can be easily identified across the entire code base and alleviated promptly as specific faulty lines of the source code are identified. Due to large size and complexity of most of the applications, source code reviews also use automated tools to identify the common vulnerabilities.
Those databases which containimportant information, such as customer names and card numbers, should also undergo strict penetration security testing. Databases can be configured so as to take advantage of different information security types and layers, such as authentication, access control, and encryption. Important piece in securing these databases is real-time monitoring. Host-based intrusion detection systems can warn of and recognize suspicious traffic. The results can be easily analyzed for the policy breaches and known security exploits.
The security breach costs the company loss of money as well as reputation. Source code reviews, security testing services and database and security event monitoring are all security controls that immensely help in protecting system against breaches, while demonstrating compliance to the security standards. It is always a good idea to invest in Information security companies because they have expert professionals to enhance security of your system.